Data Breaches: How They Happen and How to Protect Yourself

Introduction
In an era where data is often termed the ‘new oil,’ safeguarding information has become paramount. Data breaches have emerged as a pervasive threat with the increasing reliance on digital platforms. These breaches, involving the unauthorized access and exploitation of sensitive information, can lead to devastating financial losses, severe reputational damage, and exposure to legal liabilities. Understanding the dynamics of data breaches is crucial for individuals and organizations aiming to protect their valuable information. This article explores the intricacies of how data breaches occur, their potential impacts, and the vital steps needed to shield against them.
How Data Breaches Happen
Data breaches arise from a complex interplay of technological and human factors. On the technological front, vulnerabilities in software, networks, and applications are frequently targeted by cybercriminals. These weaknesses often stem from outdated software versions that lack the latest security patches, misconfigurations that provide easy access points, and unsecured third-party apps that can serve as backdoors. Attackers are constantly employing sophisticated tactics such as SQL injection, zero-day exploits, and the spread of malware to infiltrate systems and exfiltrate data. Advanced Persistent Threats (APTs), strategic targeting methods, can remain hidden in systems for extended periods while gathering and extracting sensitive data.
Human errors further exacerbate the risk of data breaches. Common mistakes like using weak passwords, sharing sensitive information through unsecured channels, and falling prey to social engineering schemes such as phishing attacks contribute significantly to breaches. Phishing alone remains one of the leading methods hackers use, leveraging fake emails and websites to deceive individuals into revealing personal credentials. The human factor in cybersecurity is often termed the weakest link, so fostering a culture of awareness and accountability around data protection is essential. Enhancing cybersecurity awareness and training within organizations is not an option but is necessary to create a vigilant workforce.
Addressing these vulnerabilities requires informed strategies and expert advice. Organizations can gain valuable insights from resources such as data breach handling advice from Fortinet, which provides comprehensive guidelines on strengthening defenses and effectively managing breaches.
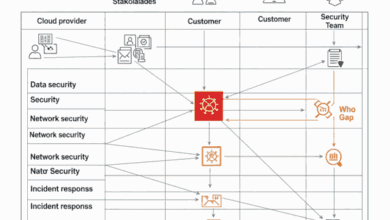
Moreover, the increasing reliance on cloud services has introduced additional challenges in securing sensitive data, as businesses must trust third-party providers to maintain robust security measures. As organizations grow and data becomes more dispersed, maintaining visibility and control over where sensitive information resides becomes more complex. Even the most well-protected systems can fall prey to undetected vulnerabilities, making implementing continuous monitoring and real-time threat detection systems crucial. Additionally, the rapid pace of technological innovation means that new vulnerabilities are constantly emerging, requiring proactive and adaptive security strategies. Lastly, legal and regulatory frameworks around data protection, such as GDPR, are evolving, necessitating that organizations stay informed and compliant to avoid costly repercussions in the event of a breach.
Protecting Against Data Breaches
Mitigating the threat of data breaches demands a holistic approach that integrates technological defenses with strategic policies and human vigilance. Below are critical strategies for robust protection:
- Regular Security Audits: Thorough security audits serve as the first line of defense by identifying potential weaknesses within networks, applications, and systems. These audits help organizations proactively address vulnerabilities before they can be exploited, ensuring that all components are secured and compliant with the latest standards.
- Employee Training: Continuous training is vital to equip employees with the knowledge and skills to recognize and appropriately respond to cyber threats. Training programs should include recognizing phishing scams, understanding secure data handling practices, and implementing reporting protocols for suspicious activities. Encouraging a security-first mindset empowers employees to act as assets rather than liabilities in cybersecurity efforts.
- Strong Password Policies: Implementing robust password policies prevents unauthorized access. Organizations should enforce complex passwords that combine letters, numbers, and symbols and require periodic updates to minimize the risk of compromise.
- Data Encryption: Encrypting sensitive data transforms it into unreadable code, ensuring the information remains inaccessible even if it is intercepted without decryption keys. Encryption should be applied when data is stored (at rest) and transmitted (in transit).
- Network Security Measures: Employing firewalls, intrusion detection systems, and intrusion prevention systems forms a network perimeter that guards against unauthorized access and attacks. Regularly updating these systems and monitoring network activity helps detect and respond to potential threats promptly.
- Access Control: Stringent access control policies ensure that only authorized personnel can access sensitive data. Implementing role-based access controls and regularly reviewing user privileges helps prevent data exposure through misuse or unauthorized access.
- Incident Response Plan: Developing a well-structured incident response plan prepares organizations to handle data breaches effectively when they occur. The plan should outline precise detection, containment, investigation, and recovery steps. Regularly testing and updating the plan ensures readiness and minimizes the impact on operations should an incident occur.
To enhance the effectiveness of these strategies, organizations should also ensure that they comply with relevant data protection regulations, such as GDPR or CCPA, to avoid legal repercussions. Collaboration with third-party vendors should be carefully managed by ensuring they adhere to the same cybersecurity standards, minimizing the risk of breaches through external channels. Continuous monitoring of systems and networks is crucial to quickly identify anomalies or breaches, allowing for immediate action to be taken. Finally, fostering a culture of cybersecurity awareness across all levels of the organization ensures that security is viewed as a shared responsibility, further reducing the likelihood of successful attacks.
Conclusion
In a digital era characterized by rapid technological advancements and increasing data value, data breaches pose significant risks that demand proactive and comprehensive mitigation strategies. By understanding the mechanisms through which data breaches occur and implementing a multi-layered defense structure, individuals and organizations can substantially lower their risk of falling prey to cyber threats.
Emphasizing regular system audits, continuous employee training, and rigorous access controls strengthens the foundation of cybersecurity efforts. Robust encryption and ongoing monitoring and incident planning ensure preparedness against potential breaches. Moreover, fostering a culture of vigilance and informed response transforms cybersecurity from a mere technical challenge into a shared organizational responsibility. Through strategic investments in technology, education, and policy, the path to safeguarding sensitive information becomes more apparent, effective, and resilient.